About SSL Stripping Attacks
Robert KimShare
SSL Certificate stripping attacks pose a serious threat to website security, making proper SSL Certificate implementation crucial.
As a leading provider of SSL Certificates, Trustico® helps organizations protect against these dangerous man-in-the-middle attacks through our comprehensive range of SSL Certificate solutions.
What is an SSL Certificate Stripping Attack?
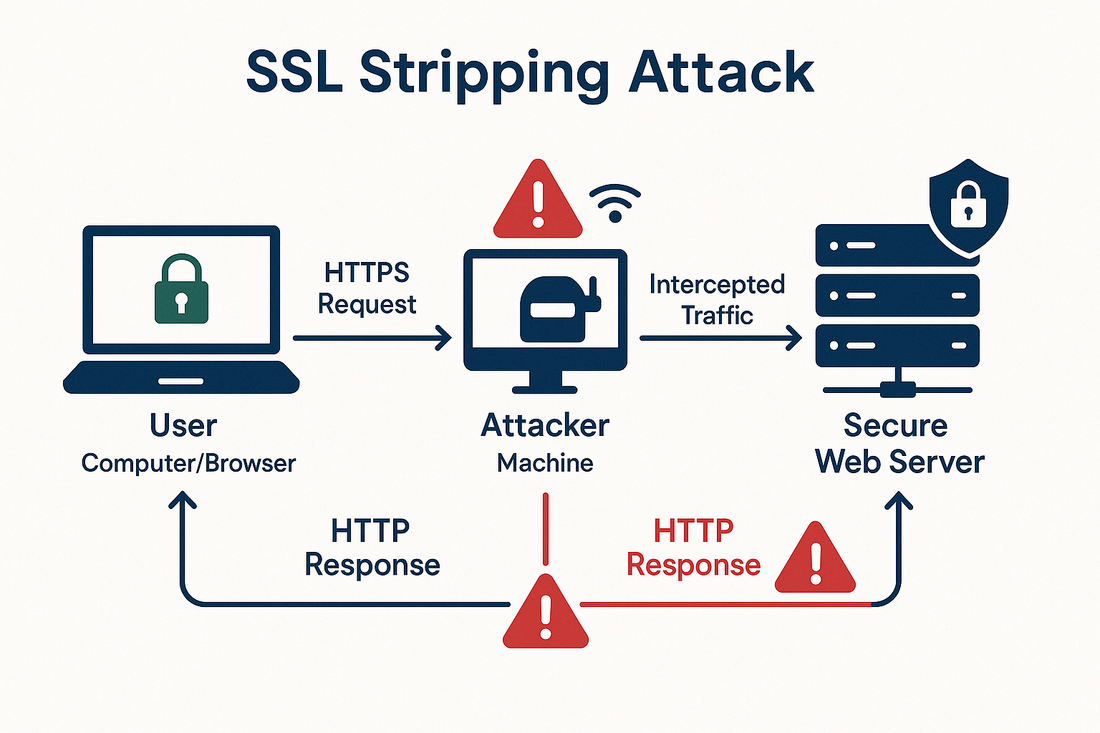
An SSL Certificate stripping attack occurs when hackers intercept and downgrade encrypted HTTPS connections to unencrypted HTTP.
This allows attackers to view sensitive data like login credentials and payment information in plain text.
Trustico® SSL Certificates help prevent these attacks by enforcing strong HTTPS encryption.
Without proper SSL Certificate protection, websites are vulnerable to having their secure connections compromised. Trustico® offers both Trustico® branded and Sectigo® branded SSL Certificates that implement the latest encryption protocols to maintain secure HTTPS connections.
Unlike some other cyber threats, SSL Certificate stripping attacks specifically target the transition point between secure and insecure communications.
These attacks exploit the initial connection request before encryption is established, making them particularly dangerous for users on public networks or those accessing websites with improper SSL Certificate implementation.
How SSL Certificate Stripping Attacks Work
Attackers typically execute SSL Certificate stripping attacks by positioning themselves between the user and the target website.
They intercept the initial HTTPS request and establish their own encrypted connection with the target server while maintaining an unencrypted connection with the user.
This allows the attacker to view and modify all traffic between the user and website. Trustico® SSL Certificates implement strict security measures like HSTS (HTTP Strict Transport Security) to prevent connection downgrades and maintain encryption.
The technical execution of an SSL Certificate stripping attack often begins with a user attempting to visit a secure website by typing the domain name without explicitly specifying "https://" in the address bar. The browser initially sends an HTTP request before being redirected to HTTPS, creating a vulnerability window.
During this vulnerable moment, the attacker intercepts the initial HTTP request and prevents the HTTPS redirect from occurring. The attacker then establishes their own HTTPS connection with the legitimate website while keeping the user on an unencrypted connection.
The result is that all traffic between the user and website passes through the attacker in unencrypted form, allowing them to view and potentially modify sensitive information. This attack succeeds because the user typically has no visual indication that their supposedly secure connection has been compromised.
Without proper SSL Certificate security measures, users may have no indication that their supposedly secure connection has been compromised.
This makes SSL Certificate stripping particularly dangerous for sensitive operations like online banking and e-commerce transactions.
Real-World Impact of SSL Certificate Stripping
The consequences of successful SSL Certificate stripping attacks can be severe for both organizations and their users.
Financial losses from compromised payment information, identity theft from stolen credentials, and damage to brand reputation are common outcomes when SSL Certificate security is breached.
E-commerce websites are particularly vulnerable to SSL Certificate stripping attacks due to the valuable payment data they process.
Without proper SSL Certificate implementation including HSTS, online stores risk exposing customer financial information to attackers.
Corporate environments face additional risks from SSL Certificate stripping attacks targeting employee credentials.
When these attacks succeed, they can provide attackers with access to internal systems and sensitive company data.
Trustico® SSL Certificates with proper implementation help prevent these security breaches.
Preventing SSL Certificate Stripping with Trustico® SSL Certificates
The most effective defense against SSL Certificate stripping is proper SSL Certificate implementation. Trustico® SSL Certificates provide essential security features for comprehensive protection against these attacks.
Forced HTTPS encryption across all pages and subdomains ensures that every connection to your website uses secure protocols. This fundamental security measure forms the foundation of protection against SSL Certificate stripping attacks by minimizing opportunities for connection downgrade.
HSTS preloading capability works with Trustico® SSL Certificates to prevent downgrade attacks by instructing browsers to always use secure connections. This critical security feature eliminates the vulnerable initial connection that attackers exploit during SSL Certificate stripping attempts.
Extended Validation SSL Certificates from Trustico® provide maximum trust indicators to users, helping them verify they're connected to legitimate websites. These visual cues serve as an additional layer of protection by making users more aware of potential security issues.
Support for the latest TLS protocols and cipher suites ensures your website uses the strongest available encryption standards. Trustico® SSL Certificates maintain compatibility with current security best practices to protect against evolving threats.
Our range of SSL Certificates includes options for websites of all sizes. From basic Domain Validation (DV) to full Extended Validation (EV) SSL Certificates, Trustico® has the right solution to protect your site.
HTTP Strict Transport Security (HSTS) is particularly important for preventing SSL Certificate stripping attacks. When properly implemented alongside Trustico® SSL Certificates, HSTS instructs browsers to always use secure connections, eliminating the vulnerable initial HTTP request that attackers exploit.
For maximum protection, Trustico® recommends implementing HSTS preloading with your SSL Certificate. This security measure registers your domain in browsers' built-in HSTS lists, ensuring that even first-time visitors connect via HTTPS, completely eliminating the vulnerability window that SSL Certificate stripping attacks exploit.
Technical Implementation of Anti-Stripping Measures
Implementing effective protection against SSL Certificate stripping requires several technical measures beyond simply installing an SSL Certificate.
The HSTS header should be configured with appropriate parameters when implementing Trustico® SSL Certificates.
A properly configured header includes a sufficient max-age directive (typically at least 31536000 seconds or one year) and the includeSubDomains directive to protect all subdomains.
For example, a proper HSTS header implementation would look like :
Strict-Transport-Security: max-age=31536000; includeSubDomains; preload
Trustico® also recommends implementing proper SSL Certificate pinning for critical applications. This technique restricts which SSL Certificates browsers will accept for your domain, providing additional protection against sophisticated attacks that might attempt to bypass standard SSL Certificate validation.
Content Security Policy (CSP) headers work alongside your Trustico® SSL Certificate to provide additional protection. A properly configured CSP can prevent mixed content warnings and ensure all resources are loaded securely, closing potential security gaps that attackers might exploit.
Best Practices for SSL Certificate Security
To maximize protection against SSL Certificate stripping and other attacks, Trustico® recommends following several important SSL Certificate best practices for comprehensive security.
Installing SSL Certificates on all public-facing domains and subdomains ensures complete coverage across your web presence. This comprehensive approach prevents attackers from exploiting unprotected areas of your website that might otherwise serve as entry points for SSL Certificate stripping attacks.
Enabling HSTS with proper configuration creates a strong defense against downgrade attacks by instructing browsers to always use secure connections. This critical security measure works alongside your Trustico® SSL Certificate to prevent the initial vulnerability that SSL Certificate stripping attacks exploit.
Keeping SSL Certificate implementations up-to-date ensures you benefit from the latest security enhancements and protections. Regular updates to your SSL Certificate configuration help defend against newly discovered vulnerabilities and attack techniques.
Monitoring SSL Certificate expiration dates prevents security gaps that could be exploited by attackers. Expired SSL Certificates trigger browser warnings and may leave your website vulnerable to various attacks including SSL Certificate stripping.
Using automated SSL Certificate management tools simplifies the maintenance of your security infrastructure. These tools help ensure timely renewals and proper configuration, reducing the risk of human error in your SSL Certificate implementation.
Implement 301 redirects from HTTP to HTTPS for all pages on your website. While this alone doesn't prevent SSL Certificate stripping attacks, it works alongside your Trustico® SSL Certificate and HSTS implementation to create a more comprehensive security posture.
Regularly test your SSL Certificate implementation using security scanning tools. These assessments can identify potential vulnerabilities in your SSL Certificate configuration before attackers can exploit them.
Detecting SSL Certificate Stripping Attempts
While prevention is the primary defense against SSL Certificate stripping, organizations should also implement detection mechanisms to identify potential attack attempts.
Network monitoring tools can help identify unusual patterns that might indicate SSL Certificate stripping activity.
User education plays an important role in detecting SSL Certificate stripping attempts. Train employees and customers to verify HTTPS connections by checking for the padlock icon and valid SSL Certificate information before entering sensitive data.
Implement logging and monitoring systems that alert security teams to potential SSL Certificate issues or unexpected connection patterns. These systems complement your Trustico® SSL Certificate implementation by providing early warning of possible security incidents.
Why Choose Trustico® SSL Certificates
As an industry leader in SSL Certificate solutions, Trustico® offers significant advantages for organizations seeking protection against SSL Certificate stripping and other security threats.
Our wide range of SSL Certificate options ensures we can provide the right security solution for any need. From small websites to enterprise applications, Trustico® offers appropriate SSL Certificate products with varying validation levels and features to match your specific requirements.
Trustico® provides both Trustico® branded and Sectigo® branded SSL Certificates, giving customers flexibility in their security implementation. This partnership with Sectigo®, a leading Certificate Authority, ensures our SSL Certificates maintain universal browser compatibility and recognition.
Fast issuance and simple installation processes minimize the time and effort required to secure your website. Trustico® streamlines the validation and deployment of SSL Certificates, helping you implement protection against SSL Certificate stripping attacks quickly and efficiently.
Expert technical support from our dedicated team ensures you receive guidance throughout your SSL Certificate lifecycle. From initial selection through implementation and renewal, Trustico® provides the assistance you need to maintain effective protection against security threats.
Competitive pricing and volume discounts make comprehensive SSL Certificate security accessible for organizations of all sizes. Trustico® believes strong security should be available to everyone, and our pricing structure reflects this commitment.
Trustico® SSL Certificates are backed by industry-leading warranty protection, providing financial assurance in the unlikely event of encryption failures or SSL Certificate mis-issuance. This additional layer of protection demonstrates our confidence in the security of our SSL Certificate solutions.
Our SSL Certificate management platform simplifies the entire SSL Certificate lifecycle, from initial purchase through installation, monitoring, and renewal. This comprehensive approach reduces administrative overhead and helps prevent security gaps caused by expired SSL Certificates.
Getting Started with Anti-Stripping Protection
Implementing protection against SSL Certificate stripping attacks begins with selecting the right SSL Certificate provider. Trustico® offers a complete range of SSL Certificate solutions to match any security requirement or budget consideration.
Begin with an assessment of your current website security to identify potential vulnerabilities to SSL Certificate stripping attacks.
Develop a comprehensive SSL Certificate security plan that includes proper implementation, HSTS configuration, regular monitoring, and employee education. This holistic approach provides the strongest protection against SSL Certificate stripping and other security threats.
Protect your website and users from SSL Certificate stripping attacks with trusted SSL Certificates from Trustico®. Our SSL Certificate solutions provide the encryption and security features needed to maintain secure HTTPS connections and prevent malicious attacks.



